Privacy & Security
Keep Your Data Safe With Compa
Unlike legacy surveys, Compa is built for the highest levels of data privacy and security.





Trusted by compensation leaders managing billion-dollar portfolios

Modern and flexible privacy standards
We built Compa with the highest privacy and security standards to protect your data.


Minimums and dominance
- All market data is aggregate
- Minimum of 3 companies and 5 data points
- Market data releases are limited by country, job, level, etc.



Peer Groups
- Peer Groups must contain 10 or more companies
- Only admins can create Peer Groups, and only companies with completed integrations are available.
- All Peer Groups require Compa approval


Advanced Rules
- Weight-by-Company reduces distortions and eliminates data dominance risk
- Minimum new companies released
- Old data mode allows access to aggregate anonymized data more than a specified number of days old
Data and privacy standards
New technology, same standards, better control
While introducing new real-time technology, Compa doesn’t alter or replace the Safe Harbor standards that have defined compensation market data for decades.
- Data privacy minimums
- Data dominance limits
- Configurable data recency and scope (“aging”)
- No pricing algorithms or recommendations
- No PII collected
- Peer Groups require Compa approval
- Data release multiple company minimums
Security for the best teams in the world
Compa is SOC 2 Type II certified and GDPR compliant. Since its founding days, Compa has worked with some of the best enterprise compensation teams to instill compliance in everything we do.
- SOC2 Type II certified
- GDPR compliant
- AWS Region US West 2 (Oregon) & US East 1 (Virginia)
- TLS 1.2+ encryption for transit
- AES-256 for rest
- No PII transferred
- SSO required
- No security breaches

Our Data Privacy Promise
When the market moves fast, you can't rely on surveys. Remove uncertainty and gain confidence with Compa.


Increase Competitiveness
Information technology, software, cloud computing, data, and security companies are shifting to software-delivered market data by Compa.


Eliminate Privacy Risk
Modern privacy protocols minimize data requirements and protect sensitive data.


Maintain Compliance
Compa adheres to industry antitrust standards and complies with GDPR requirements.


Not Another Algorithm
Compa provides insights to comp teams to make decisions — it does not recommend actual pay amounts.


Establish New Standards
Using industry-leading third-party skills ontologies, Compa extracts skills from job descriptions. The extracted skills are analyzed through Compa’s proprietary software SkillGuard.


Collaborative Governance
We regularly collaborate with comp teams to review privacy standards and gather feedback on new privacy features.
Compa’s approach to Safe Harbor
Compa’s approach aligns with current DOJ and FTC enforcement priorities to promote fair competition and protect data privacy.
Our platform aggregates and anonymizes compensation data from participating employers, applying safeguards to prevent re-identification, limits data dominance, and supports compliant market insights.
The Highest Standards To Protect Your Data
We have an Information Security Program in place that is communicated throughout the organization. Our Information Security Program follows the criteria set forth by the SOC 2 Framework. SOC 2 is a widely known information security auditing procedure created by the American Institute of Certified Public Accountants.
Our organization undergoes independent third-party assessments to test our security and compliance controls.
We perform an independent third-party penetration at least annually to ensure that the security posture of our services is uncompromised.
Roles and responsibilities related to our Information Security Program and the protection of our customer's data are well defined and documented. Our team members are required to review and accept all of the security policies.
Our team members are required to go through employee security awareness training covering industry standard practices and information security topics such as phishing and password management.
All team members are required to sign and adhere to an industry standard confidentiality agreement prior to their first day of work.
We perform background checks on all new team members in accordance with local laws.
All of our services are hosted with Amazon Web Services (AWS). They employ a robust security program with multiple certifications. For more information on our provider's security processes, please visit AWS Security.
All of our data is hosted on Amazon Web Services (AWS) databases. These databases are all located in the United States. Please reference the above vendor specific documentation linked above for more information.
All databases are encrypted at rest.
Our applications encrypt in transit with TLS/SSL only.
We perform vulnerability scanning and actively monitor for threats.
We actively monitor and log various cloud services.
We use our data hosting provider's backup services to reduce any risk of data loss in the event of a hardware failure. We utilize monitoring services to alert the team in the event of any failures affecting users.
We have a process for handling information security events which includes escalation procedures, rapid mitigation and communication.
Access to cloud infrastructure and other sensitive tools are limited to authorized employees who require it for their role.
Where available we have Single Sign-on (SSO), 2-factor authentication (2FA) and strong password policies to ensure access to cloud services are protected.
We follow the principle of least privilege with respect to identity and access management.
We perform quarterly access reviews of all team members with access to sensitive systems.
All team members are required to adhere to a minimum set of password requirements and complexity for access.
All company issued laptops utilize a password manager for team members to manage passwords and maintain password complexity.
We undergo at least annual risk assessments to identify any potential threats, including considerations for fraud.
Vendor risk is determined and the appropriate vendor reviews are performed prior to authorizing a new vendor.
Learn more about Compa's approach to data privacy
Compa’s platform and infrastructure are hosted on Amazon Web Services (AWS) in the United States. All customer and market data are processed within secure, access-controlled environments that meet leading industry security and privacy standards.
Data processing is performed in accordance with our Master Services Agreement (MSA) and Data Processing Addendum (DPA), and in compliance with GDPR, CCPA, and other applicable data protection regulations.
Compa supports customers’ regional and contractual requirements for data residency, retention, and deletion, and provide supporting documentation through the Compa Trust Center.
Subprocessors
Compa engages a limited number of trusted subprocessors—third-party service providers that support infrastructure and platform operations. Each subprocessor is carefully vetted for security, privacy, and regulatory compliance, and is bound by written data protection terms consistent with Compa’s contractual and legal obligations.
A current list of approved subprocessors, including their purpose and geographic location, is maintained and publicly available in the Compa Trust Center.
No. SOC 1 Type 2 does not apply to Compa’s business or services.
SOC 1 reports are designed for organizations that provide financial reporting-related services, such as payroll processors or accounting platforms whose controls could impact a customer’s financial statements. Because Compa does not process or influence customers’ financial reporting data, a SOC 1 audit is not applicable.
Compa engages an independent, third-party security firm to conduct a formal penetration test annually.
Each assessment includes both application-level and infrastructure-level testing, performed against our production environment in accordance with industry best practices such as OWASP Top 10 and NIST methodologies. Findings, if any, are tracked to resolution through Compa’s secure development lifecycle and verified as remediated.
A summary of the most recent penetration test results is available to customers under NDA through the Compa Trust Center.
Yes. All Compa employees complete security and privacy training as part of their onboarding process.
Compa also provides annual refresher training and additional topical or role-based sessions as needed to reinforce key concepts and support continuous awareness.
This training ensures that every employee understands their responsibilities in protecting customer data and maintaining Compa’s high security and privacy standards.
For many years, U.S. Department of Justice (DOJ) and Federal Trade Commission (FTC) guidance led HR leaders to believe that compensation data could only be shared if it was aggregated and at least 90 days old. That standard shifted in February 2023, when the DOJ withdrew its 1996 Healthcare Safe Harbor statement. Then, in January 2025, the DOJ and FTC also rescinded the 2016 Antitrust Guidance for Human Resource Professionals.
These actions reflect an evolving regulatory environment and a move away from rigid “safe harbor” assumptions toward a broader, case-by-case evaluation of how compensation data is shared. While the specific safe harbor criteria no longer apply, the agencies’ enforcement focus remains the same—preventing employer collusion and protecting healthy competition in labor markets.
Compa’s approach aligns with both the spirit and the intent of current DOJ and FTC enforcement priorities. The Compa platform uses aggregated, anonymized compensation data from hundreds of participating employers, with robust safeguards to ensure statistical sufficiency, data privacy, and fair-market representation. This design supports transparent, competitive, and compliant pay practices—without enabling coordination or restricting competition.Compa’s solution is built for trust and compliance. Acting as a neutral third-party intermediary, Compa replaces risky one-to-one data exchanges with a secure, automated system validated by independent experts at NCC Group. The platform’s secure-by-design architecture prevents disaggregation or re-identification of data, applies parallel adoption rules to delay new data releases until it can be combined with data from other employers, and enforces visibility thresholds. Compa’s multi-layered aggregation and dominance controls ensure that no single employer can influence market outputs. These built-in safeguards, coupled with a privacy-by-default model and continuous compliance monitoring, give customers confidence that market insights remain competitive, compliant, and safe.
Compa is built with privacy by design. Our platform and processes are designed to protect both employer and candidate information, without relying on personally identifiable information (PII). Compa does not require, process, or store PII as part of market data generation.
Our commitments to privacy and data protection are formalized in Compa’s Master Services Agreement (MSA) and Data Processing Addendum (DPA), and are backed by our compliance with GDPR and other leading data privacy standards.
At the platform level, Compa applies multi-layered privacy and data sufficiency controls to ensure data integrity and prevent re-identification:
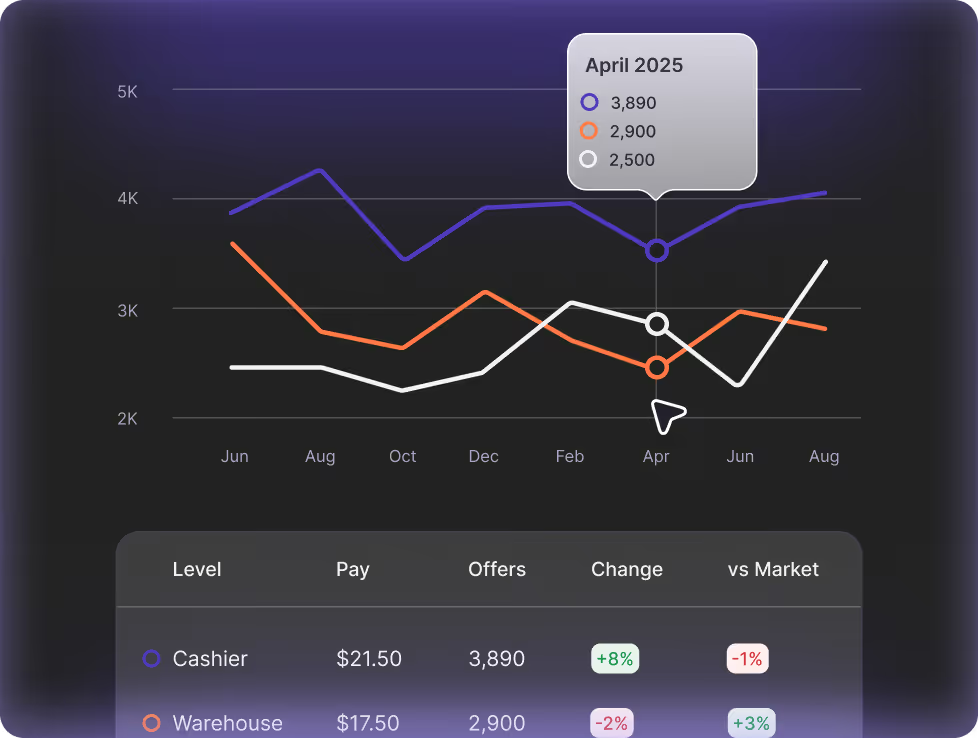
- Minimum participant thresholds (n-counts): Market data is only shown when sufficient data points are available across selected dimensions (such as job family, level, and location).
- Weighted data modes: Users can view aggregated data either by number of offers (“weight by offers”) or by participating companies (“weight by companies”), ensuring balanced representation.
- Market share limits: No single company ever represents more than a small, defined percentage of any aggregated market dataset.
- Peer group protections: Data visibility requires a minimum number of participating companies, and additional contribution percentage thresholds prevent any one participant from dominating a peer group.
These safeguards ensure that every insight derived from Compa reflects a statistically valid, anonymous view of the market—never the data of an individual company or person.
For more details, visit our Trust Center, where you can access privacy documentation, certifications, and security reports.
Yes. Compa complies with both the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR).
Under these frameworks, Compa acts as a data processor, while Compa’s customers remain the data controllers. This means customers retain full ownership and control over their data. Compa processes data strictly in accordance with customer instructions and the terms outlined in our Data Processing Addendum (DPA).
Compa’s privacy program is built on a privacy-by-design foundation. Compa does not require or use personally identifiable information (PII) to generate market data. All data within the Compa platform is aggregated, anonymized, and governed by strict access controls, ensuring compliance with applicable data protection laws.
Compa also supports customers in fulfilling their privacy obligations, including data subject rights requests and other CCPA or GDPR requirements, as needed.
For more information, visit the Compa Trust Center to access privacy documentation and compliance certifications.
Yes. Compa is SOC 2 Type 2 certified.
Compa’s independent SOC 2 Type 2 audit, conducted by an accredited third party, verifies that Compa maintains effective controls aligned with the AICPA Trust Services Criteria for security.
This certification demonstrates Compa’s commitment to safeguarding customer data through continuous monitoring, formalized policies, and secure-by-design engineering practices.
The current SOC 2 Type 2 report and supporting compliance documentation are available through the Compa Trust Center.
Yes. Compa uses industry-standard encryption to protect all customer data both in transit and at rest.
- In transit: All data transmitted within or to the Compa platform is encrypted using TLS 1.2 or higher.
- At rest: All stored data, including backups, is encrypted using AES-256 encryption.
Encryption is always on throughout every transport tier and storage layer of the Compa platform. These controls are enforced by default and continuously monitored as part of our SOC 2 Type 2 security program.
Compa uses AWS-owned encryption keys, which are fully managed by Amazon Web Services (AWS).
This model ensures that encryption is always on by default across all AWS services used by Compa, including data stored in S3, EBS, and RDS. AWS-owned keys are automatically created, stored, rotated, and secured by hardware security modules (HSMs) that meet FIPS 140-3 criteria.
Because key management is handled entirely by AWS, Compa inherits AWS’s strong, continuously validated encryption and key protection controls without requiring any manual key configuration or rotation. All encryption at rest and in transit within the Compa platform leverages these AWS-managed safeguards.
Access to customer data within Compa is strictly limited and governed by the principle of least privilege.
A restricted group of authorized personnel may access customer data when required for legitimate operational reasons such as system maintenance, customer support, or security investigations. All access is role-based, logged, and continuously monitored.
Compa employees do not have access to customer market data content beyond what is necessary to operate and secure the platform. Production data access requires multi-factor authentication, approval, and is protected through network segmentation and strong identity controls.
Compa does not sell, share, or use customer data for any purpose other than delivering the contracted services.
More information about Compa’s security, privacy, and compliance program can be found in the Compa Trust Center.
The Trust Center provides access to Compa’s security documentation, certifications, audit reports, and policies, along with real-time updates on the company’s compliance posture and data protection practices.